Top 5 Most Dangerous Computer viruses in the world latest list 2018.
Top 5 Most Dangerous Computer viruses in the world latest list 2018.
Hello friends if you have a PC or laptop then you must heard of word "virus". When we heard about virus the first thing that comes in our mind is our laptop or PC, we does not want any virus to come in our laptop otherwise it will destroy our laptop completely and this virus are very hard to delete from computer.
You are often scared of computer viruses when you do not have viruses in your computer. Virus causes a lot of damage to the computer. Because of the virus, all the files in your computer are corrupted. It deletes all the photos, videos, documents, passwords, and all the things present in the computer. We will tell you about some dangerous viruses which are huge losses for your computer. Let's know about the world's most dangerous computer virus.
As soon as it spreads, the computer gets corrupted and all the files are deleted. It comes like a generic mail in which people have started to open it by having I love u written and the virus spreads.
The ILOVEYOU infection arrives in an email note with "I LOVE YOU" in the title and contains a connection that, when opened, results in the message being re-sent to everybody in the beneficiary's Microsoft Outlook address book and, maybe more truly, the loss of each JPEG, MP3, and certain different records on the beneficiary's hard circle. Since Microsoft Outlook is broadly introduced as the email handler in corporate systems, the ILOVEYOU infection can spread quickly from client to client inside an organization. On May 4, 2000, the infection spread so rapidly that email must be closed down in various significant ventures, for example, the Ford Motor Company. The infection came to an expected 45 million clients in a solitary day.
Yankeedoodle is named for the tune it plays. In Bulgaria, it is designated "TP44VIR". The infection has additionally been known as the "Five o'clock infection" as a result of its payload.
First showing up on September 18, 2001, Nimda is a PC infection that caused movement stoppages as it undulated over the Internet, spreading through four distinct techniques, contaminating PCs containing Microsoft's Web server, Internet Information Server (IIS), and PC clients who opened an email connection. Like various antecedent infections, Nimda's payload gives off an impression of being simply the activity stoppage - that is, it doesn't seem to pulverize records or cause hurt other than the significant time that might be lost to the abating or loss of movement known as dissent of-benefit and the reestablishing of contaminated frameworks. With its multi-pronged assault, Nimda seems, by all accounts, to be the most troublesome infection of its compose that has yet showed up. Its name (in reverse for "administrator") obviously alludes to an "admin.dll" record that, when run, keeps on proliferating the infection.This virus was the only fastest spreading virus in the 22-minute Internet on the Internet. The main motive of this virus is to stop Internet traffic and to attack on DoS.
The Morris worm was a worm outlined by Robert Tappan Morris that was discharged on November second, 1988. It is infamous for being one of the first, if not the primary, PC worms appropriated on the web.
Morris, a Cornell graduate understudy, probably composed the worm to perceive how rapidly it could spread. A bug in his code tainted frameworks all through the web at a quicker pace than Morris initially expected, and his worm wound up contaminating an expected 10 percent of the web. The final product was real harm and broad blackouts.
This term is otherwise called the colossal worm or the web worm.
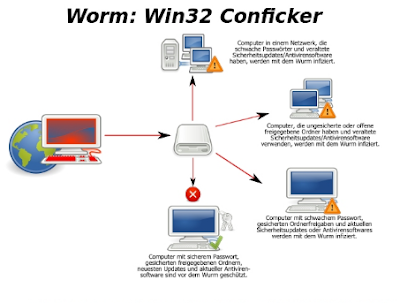
Conficker is a quick spreading worm that objectives a helplessness (MS08-067) in Windows working frameworks.
Otherwise called Downadup, Conficker was found in November 2008. Since that time, Conficker has tainted a large number of PCs and built up the framework for a botnet.
The worm is planned to contact control PCs and, probably, complete some further activity on April 1. A few specialists have theorized that the aggressors will rent parts of the botnet to lawbreakers who will utilize them for spam, data fraud, phishing misuses and different noxious exercises.
Like most current malware, Conficker is a mixed risk, joining highlights of a few distinct methodologies. When Conficker taints a PC, it handicaps numerous security highlights and programmed reinforcement settings, erases reestablish indicates and opens associations get guidelines from a remote PC. Once the main PC is designed, Conficker utilizes it to access whatever remains of the system.
Conficker can spread by a few means, replicating itself to shared organizers, for instance, or misusing the AutoRun utility for removable media. There are three variations of Conficker. Conficker C, the latest adaptation, misuses distributed systems administration capacities to upgrade its spread.
So, friends this are the Top 5 Most Dangerous Computer viruses in the world latest list 2018,
Hello friends if you have a PC or laptop then you must heard of word "virus". When we heard about virus the first thing that comes in our mind is our laptop or PC, we does not want any virus to come in our laptop otherwise it will destroy our laptop completely and this virus are very hard to delete from computer.
You are often scared of computer viruses when you do not have viruses in your computer. Virus causes a lot of damage to the computer. Because of the virus, all the files in your computer are corrupted. It deletes all the photos, videos, documents, passwords, and all the things present in the computer. We will tell you about some dangerous viruses which are huge losses for your computer. Let's know about the world's most dangerous computer virus.
Top 5 Most Dangerous Computer viruses in the world latest list 2018.
1. I LOVE YOU
I love you, this virus has ruined thousands of computers. This virus comes through a mail whose subject contains I love you. Inside there is an attachment with a love letter for u. As soon as clicking on it, the virus spreads throughout the computer like a termite.As soon as it spreads, the computer gets corrupted and all the files are deleted. It comes like a generic mail in which people have started to open it by having I love u written and the virus spreads.
The ILOVEYOU infection arrives in an email note with "I LOVE YOU" in the title and contains a connection that, when opened, results in the message being re-sent to everybody in the beneficiary's Microsoft Outlook address book and, maybe more truly, the loss of each JPEG, MP3, and certain different records on the beneficiary's hard circle. Since Microsoft Outlook is broadly introduced as the email handler in corporate systems, the ILOVEYOU infection can spread quickly from client to client inside an organization. On May 4, 2000, the infection spread so rapidly that email must be closed down in various significant ventures, for example, the Ford Motor Company. The infection came to an expected 45 million clients in a solitary day.
2. Yankee Doodle
Yankee Doodle is also a very dangerous virus. It was made in 1989 by a bulzerier hacker. This virus creates a computer's memory store as soon as it gets to the computer. Yankee Doodle transitions all .com and .exe files. If this virus is in the computer then at 4 o'clock, it starts playing as a "Yankee Doodle" alarm.Yankeedoodle is named for the tune it plays. In Bulgaria, it is designated "TP44VIR". The infection has additionally been known as the "Five o'clock infection" as a result of its payload.
3.Nimda
Nimda Virus was invented in 2001. The name of this virus is made from the English word admin. admin will reverse the word will become the name of this virus. The following virus took advantage of email, server vulnerabilities, share folders and files to spread itself.First showing up on September 18, 2001, Nimda is a PC infection that caused movement stoppages as it undulated over the Internet, spreading through four distinct techniques, contaminating PCs containing Microsoft's Web server, Internet Information Server (IIS), and PC clients who opened an email connection. Like various antecedent infections, Nimda's payload gives off an impression of being simply the activity stoppage - that is, it doesn't seem to pulverize records or cause hurt other than the significant time that might be lost to the abating or loss of movement known as dissent of-benefit and the reestablishing of contaminated frameworks. With its multi-pronged assault, Nimda seems, by all accounts, to be the most troublesome infection of its compose that has yet showed up. Its name (in reverse for "administrator") obviously alludes to an "admin.dll" record that, when run, keeps on proliferating the infection.This virus was the only fastest spreading virus in the 22-minute Internet on the Internet. The main motive of this virus is to stop Internet traffic and to attack on DoS.
4.Morris Worm
Morris Worm virus was invented in 1988 by a student of Kernel University. When the virus began to spread, 60,000 computers were attached to the Internet and the virus showed its effect on 10%. The virus has the capability to slow down the computer to a very low level, so that the computer is not worth any work.The Morris worm was a worm outlined by Robert Tappan Morris that was discharged on November second, 1988. It is infamous for being one of the first, if not the primary, PC worms appropriated on the web.
Morris, a Cornell graduate understudy, probably composed the worm to perceive how rapidly it could spread. A bug in his code tainted frameworks all through the web at a quicker pace than Morris initially expected, and his worm wound up contaminating an expected 10 percent of the web. The final product was real harm and broad blackouts.
This term is otherwise called the colossal worm or the web worm.
5.Conficker
Conficker is also known as DownUp, Downadep and Kido. It is a type of computer virus that usually targets the Microsoft Windows operating system. Nowadays most people use this Windows. It laid a trap in the computer of 190 countries, which resulted in loss of home and work of corporates and government.Conficker is a quick spreading worm that objectives a helplessness (MS08-067) in Windows working frameworks.
Otherwise called Downadup, Conficker was found in November 2008. Since that time, Conficker has tainted a large number of PCs and built up the framework for a botnet.
The worm is planned to contact control PCs and, probably, complete some further activity on April 1. A few specialists have theorized that the aggressors will rent parts of the botnet to lawbreakers who will utilize them for spam, data fraud, phishing misuses and different noxious exercises.
Like most current malware, Conficker is a mixed risk, joining highlights of a few distinct methodologies. When Conficker taints a PC, it handicaps numerous security highlights and programmed reinforcement settings, erases reestablish indicates and opens associations get guidelines from a remote PC. Once the main PC is designed, Conficker utilizes it to access whatever remains of the system.
Conficker can spread by a few means, replicating itself to shared organizers, for instance, or misusing the AutoRun utility for removable media. There are three variations of Conficker. Conficker C, the latest adaptation, misuses distributed systems administration capacities to upgrade its spread.
So, friends this are the Top 5 Most Dangerous Computer viruses in the world latest list 2018,








Post a Comment